N. Korea spreads malware during fake video job interviews
N. Korea spreads malware during fake video job interviews
Posted August. 10, 2023 08:23,
Updated August. 10, 2023 08:23
North Korea reportedly offered a fake career job interview to an employee of a cryptocurrency company with the promise of a high salary while trying to hack the employee’s personal computer by spreading malware during the interview. North Korea's hacking methods are becoming bolder and more sophisticated as it funds much of its nuclear and missile development with cryptocurrency stolen through cybercrime. While the U.S. and South Korea have intensified their collaborative efforts to tackle North Korea's cyber threats, there are growing concerns about hacking damage to South Korean companies.
On its website, Estonian cryptocurrency exchange CoinsPaid announced Monday the results of an investigation into the theft of $37.3 million in cryptocurrency by North Korean hackers on July 22.
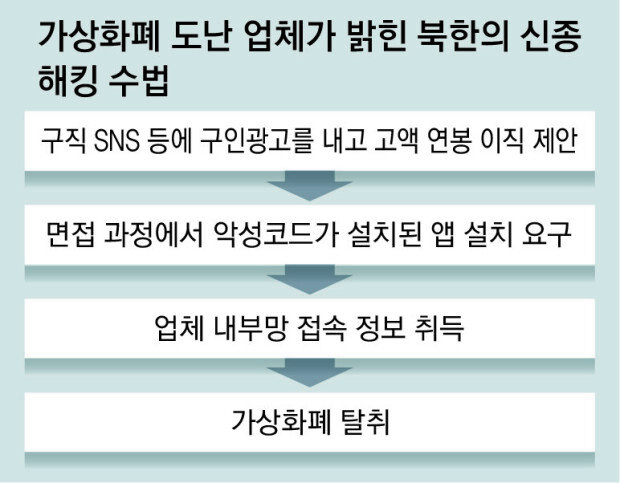
According to the announcement, in June and July, employees of the company received a job offer from a company through LinkedIn, a social media channel for jobs and recruitment, that promised a high salary of 16,000 to 24,000 dollars per month. Unaware that the job was fake, an employee accepted the offer and was asked to install a specific application (app) during the video interview. The app contained malware, and the hackers obtained the employee's personal information that enables access to the company's internal network and stole cryptocurrency.
Prior to this, the hackers had conducted more than a dozen spearphishing (a phishing method that extracts information via email) attempts since March to attack vulnerabilities in the company's systems but failed. This time, the hackers changed their tactics by utilizing social media. “The system is designed in a way that makes it impossible to hack without gaining access to employee computers,” CoinsPaid said. "The hackers spent six months learning details about the organization's structure and team members before launching the attack."
The company also called the hack "the same hacking pattern as Lazarus." Lazarus, founded in 2007 under North Korea's Reconnaissance General Bureau, is known for high-profile hacks against Sony Pictures in 2014 and the central bank of Bangladesh in 2016. In February, the South Korean government designated Lazarus as a target of its cyber sanctions against North Korea.
Kyu-Jin Shin newjin@donga.com