‘Lineage’ security breach by N. Korean hackers revealed in 10 years
‘Lineage’ security breach by N. Korean hackers revealed in 10 years
Posted February. 05, 2025 07:47,
Updated February. 05, 2025 07:47
It has been revealed that 10 years ago, the operator of an illegal private server for the popular game Lineage collaborated with a North Korean hacker to purchase and use a program that bypassed security measures. The hacker was affiliated with an organization under “Room 39,” a North Korean foreign currency-earning entity, raising concerns that the transaction’s proceeds may have contributed to North Korean regime funds.
According to legal sources on Tuesday, the 9th Criminal Division of the Seoul Western District Court sentenced Mr. Oh to one year in prison and a one-year suspension of qualifications on December 11 last year for violating the National Security Act. Both Mr. Oh and the prosecution appealed the ruling, and the case is currently under appeal.
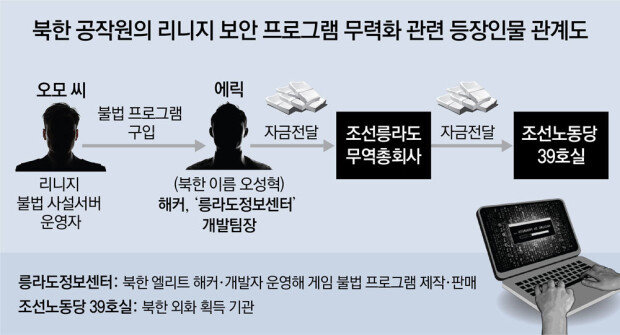
Court records show that Mr. Oh operated the unofficial Potato Server, which illegally copied and ran Lineage. Facing operational difficulties due to enhanced security measures on the official server, he was introduced to North Korean hacker ‘Eric,’ whose Korean name is Oh Seong-hyeok, in early 2014 through a business associate. It is known that illegal private servers allow for easier and cheaper gameplay compared to official servers.
Eric was a development team leader at the Rungrado Information Center under Room 39, which funds the North Korean regime. Based in Pyongyang, the information center operated an office in China disguised as a trading company to generate foreign currency. Eric developed and sold Mr. Oh a core executable program that disabled Lineage's security, allowing access to the illegal server.
Between October 2014 and March 2015, Mr. Oh transferred 23.8 million won to a Chinese Gongsang Bank account designated by Eric. The funds are believed to have been funneled through Room 39 and ultimately contributed to North Korean leader Kim Jong Un’s regime.
The court highlighted the severity of the crime, stating, “The defendant was aware that the other party had the capability to conduct cyber terrorism against South Korea by hacking national security-related information.” The ruling also noted that North Korea trains around 300 hacking specialists annually, deploying them to cyber units targeting South Korea.
최원영 기자 o0@donga.com